Funny Videos of Ceos Misusing Money
This module is a resources for lecturers
Estimator-related offences
Computer-related offences include cyber-enabled crimes committed "for personal or financial proceeds or damage" (UNODC, 2013, p. 16). The cybercrimes included under this category "focus … on acts for which the utilize of a computer system [or digital device] is inherent to the modus operandi" of the criminal (UNODC, 2013, p. 17). The 2013 UNODC Draft Comprehensive Study on Cybercrime identified the following cybercrimes in this wide category (p. sixteen):
- Computer-related fraud or forgery
- Computer-related identity offences
- Sending or decision-making sending of spam
- Computer-related copyright or trademark offences
- Computer-related acts causing personal harm
- Computer-related solicitation or "grooming" of children
Figurer‐related fraud or forgery
Nether the Council of Europe Cybercrime Convention, fraud and forgery are considered function of the computer-related offences (i.eastward., calculator-related forgery and computer-related fraud). Article 7 of the Quango of Europe Cybercrime Convention defines computer-related forgery as "intentional… and without correct, the input, alteration, deletion, or suppression of computer information, resulting in inauthentic data with the intent that it exist considered or acted upon for legal purposes as if information technology were authentic, regardless whether or not the data is direct readable and intelligible." This cybercrime is likewise prohibited under Commodity x of the Arab Convention on Combating Information Technology Offences.
Computer-related forgery involves impersonation of legitimate individuals, government, agencies, and other entities online for fraudulent purposes. Cybercriminals can impersonate people from legitimate organizations and agencies in order to trick them into revealing personal data and providing the offenders with money, goods and/or services. The email sender pretends to be from a legitimate organization or agency in an try to get users to trust the content and follow the instructions of the electronic mail. Either the email is sent from a spoofed email address (designed to look similar an authentic e-mail from the organization or agency) or from a domain name similar to the legitimate organization or agency (with a few minor variations).
A common technique used is the sending of an email to targets with a website link for users to click on, which might either download malware onto the users' digital devices or sends users to a malicious website that is designed to steal users' credentials ( phishing). The "spoofed" website (or pharmed website) looks like the organization's and/or agency's website and prompts the user to input login credentials. The e-mail provides different prompts to arm-twist fearfulness, panic and/or a sense of urgency in order to get the user to reply to the electronic mail (and complete the tasks requested in the electronic mail) as soon as possible (come across Image 1 beneath), such equally the need to update personal data to receive funds or other benefits, warnings of fraudulent activity on the user'south account, and other events requiring the target'due south immediate attention.
Image 1: Screenshot phishing email
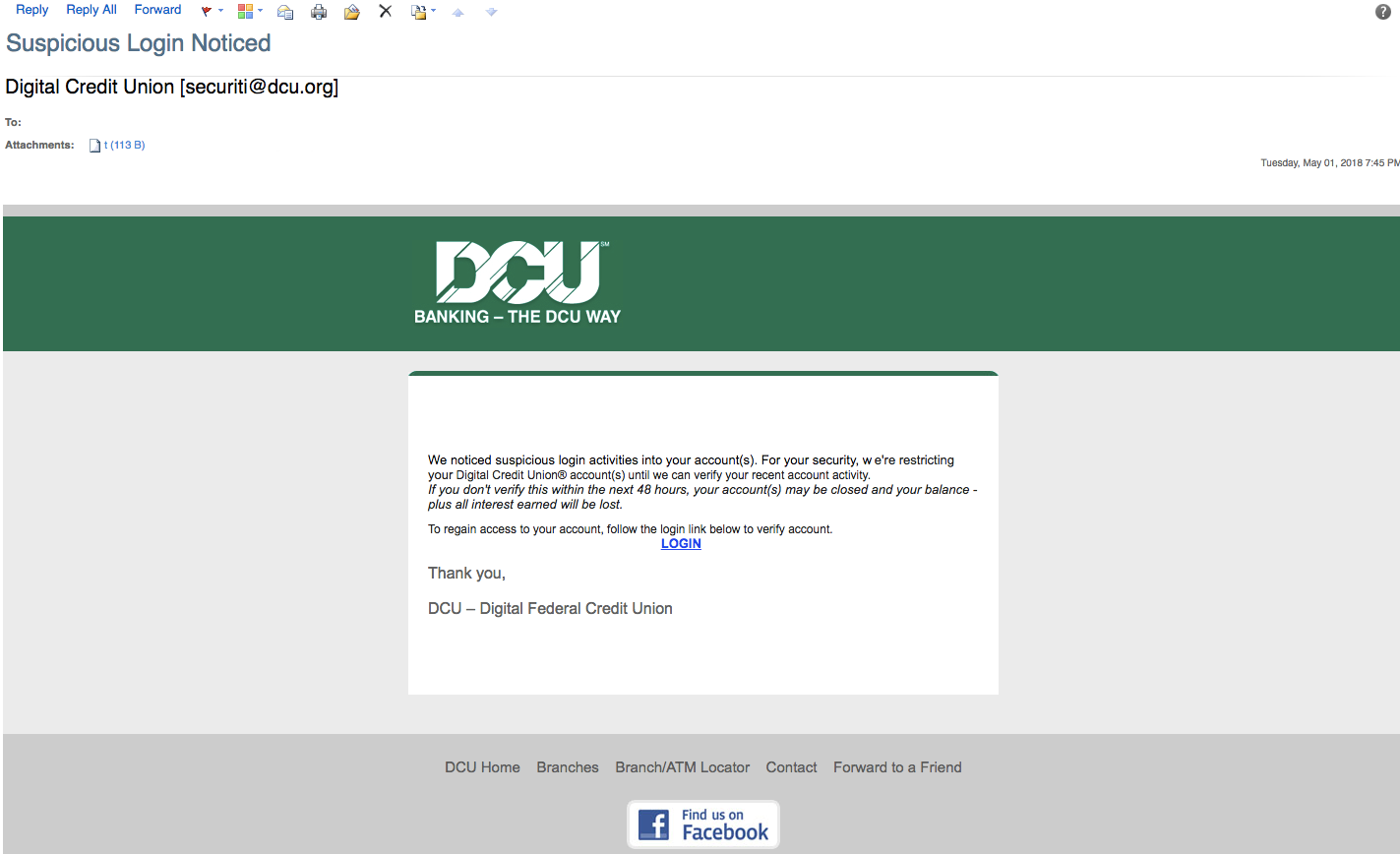
This tactic is not targeted, the email is sent en masse to catch as many victims every bit possible. A targeted version of phishing is known equally spearphishing. This form of fraud occurs when perpetrators are familiar with the inner workings and positions of company employees and transport targeted emails to employees to trick them into revealing information and/or sending coin to the perpetrators. Some other technique involves cybercriminals pretending to be higher level executives in a company (role of the C-suite - Chief Executive Officer, Chief Financial Officeholder and Chief Security Officer), lawyers, accountants, and others in positions of authority and trust, in social club to trick employees into sending them funds. This tactic is known as whaling considering it yields the highest payout.
The US toy company Mattel was a victim of whaling. The cybercriminals behind this attack had been surreptitiously monitoring the visitor'south networks and communications for months prior to the incident. Subsequently an announcement was made that a new CEO was appointed, the cybercriminals used the identity of the new CEO (Christopher Sinclair) to perpetrate the attack. Particularly, the cybercriminals sent a message as Christopher Sinclair asking the recipient to corroborate a iii-million-dollar transfer to a bank in Wenzhou, Communist china, to pay a Chinese supplier. As the asking came from the CEO, the employee transferred the money only afterward contacted the CEO about it. The CEO denied making the request. Mattel subsequently contacted Usa law enforcement, the U.s.a. Federal Bureau of Investigation, their bank, and Chinese law enforcement authorities (Ragan, 2016). The timing of the incident (the money had been transferred on the eve of a vacation) gave Chinese authorities time to freeze the accounts before the banks opened, enabling Mattel to recover its coin.
Did you lot know?
Phishing via telecommunications is known as vishing (because a voicemail message is left that is designed to get the target to call a number and provide personal and/or financial data), and phishing via text messaging is known as smishing (or SMS phishing).
Article viii of the Council of Europe Convention on Cybercrime defines computer-related fraud as "intentional… and without right, the causing of a loss of property to another person by…any input, amending, deletion or suppression of computer data,…[and/or] whatever interference with the functioning of a computer system, with fraudulent or dishonest intent of procuring, without right, an economic do good for oneself or for another person." This cybercrime is also prohibited under Article 11 of the Arab Convention on Combating Information technology Offences.
Figurer-related fraud includes many online swindles that involve false or misleading promises of love and companionship ( catphishing), property (through inheritance scams), and money and wealth (through lottery scams, investment fraud, inheritance scams, etc.). The ultimate goal of these scams is to trick the victim into revealing or otherwise providing personal information and/or funds to the perpetrator (a form of social engineering science fraud). This tactic, as the name implies, uses social technology (a term popularized by a US hacker, Kevin Mitnick), the practice "of manipulating, deceiving, influencing, or tricking individuals into divulging confidential information or performing acts that will do good the social engineer in some style" (Maras, 2014, p. 141).
The most well-known computer-related fraud involves a request for an advance fee to complete a transfer, deposit or other transaction in substitution for a larger sum of money ( advanced fee fraud a.k.a., 419 scam). While the story of the perpetrators changes (they pose as government officials, bank officials, lawyers, etc.), the aforementioned tactic is used - a request for a minor corporeality of money, in exchange for a large amount of money.
Reckoner‐related identity offences and spam
In add-on to the online schemes, financial (or economical) fraud, such every bit depository financial institution fraud, e-mail fraud, and debit and credit card fraud, is also perpetrated online. For case, debit and credit carte information that has been illicitly obtained is sold, shared, and used online. A 2018 international cybercrime operation led to the closure of one of the near well-known online illicit carding forums, Infraud, which sold and shared stolen credit and debit card data and banking information (DOJ, 2018). The personal, medical, and financial information bought, sold, and traded online could be used to commit other crimes, such as identity-related criminal offense, whereby the perpetrator unlawfully assumes and/or misappropriates the identity of the victim and/or uses the identity and/or information associated with the identity for illicit purposes (UNODC, n.d.). The type of data targeted by criminals includes identity-related information, such every bit identification numbers (e.1000., social security numbers in the Us), identity documents (e.g., passports, national identifications, driver'due south licenses, and birth certificates), and online credentials (i.e., usernames and passwords) (UNODC, 2011, p. 12-15). Identity-related law-breaking may or may not exist financially motivated. For case, fraudulent identity documents (due east.1000., passports) could be purchased online for use in travel (United nations-CCPCJ, 2017, p. 4). These types of crimes, as well as economic fraud, are facilitated online through the sending of unsolicited emails ( spam), newsletters, and messages with links to websites, which are designed to mislead users and trick them into opening the emails and newsletters or clicking on links in the emails, which may incorporate malware or exist designed to send them to pharmed websites.
Computer‐related copyright or trademark offences
Article 10 of the Council of Europe Cybercrime Convention criminalizes "offences related to infringements of copyright and related rights." Similarly, Article 17 of the Arab Convention on Combating Information Engineering Offences prohibits "offences related to copyrights and next rights."Copyrights "chronicle … to literary and artistic creations, such as books, music, paintings and sculptures, films and technology-based works (such as figurer programs and electronic databases)" (WIPO, 2016, p. 4).
There are several international treaties relating to copyright protection, including the Berne Convention for the Protection of Literary and Artistic Works of 1886, the World Intellectual Property Organisation (WIPO) Agreement on Trade-Related Aspects of Intellectual Belongings Rights of 1994, and the WIPO Copyright Treaty of 1996. Regional laws also be with respect to intellectual property. A notable example of the infringement of copyright protection is digital piracy (e.g., the unauthorized copying, duplication, or distribution of a movie protected by copyright constabulary).
Copyrighted works are considered a class of intellectual belongings, which is defined by WIPO as "creations of the listen, such as inventions; literary and artistic works; designs; and symbols, names and images used in commerce." Article 2(viii) of the Convention Establishing the Globe Intellectual Holding Organization (WIPO) of 1967 holds that
intellectual property…include[southward] rights relating to: … literary, creative and scientific works, … performances of performing artists, phonograms and broadcasts, … inventions in all fields of human endeavour, … scientific discoveries, … industrial designs, … trademarks, service marks and commercial names and designations, … protection against unfair competition, and all other rights resulting from intellectual activity in the industrial, scientific, literary or creative fields.
Intellectual property, therefore, includes not only copyrights (e.g., books, music, picture show, software, etc.), simply too trademarks (i.east., names, symbols or logos belonging to a brand, service, or good), patents (i.e., novel and unique creations, innovations, and inventions) and merchandise secrets (i.e., valuable information about business organisation processes and practices that are surreptitious and protect the business' competitive advantage). Intellectual holding is explored in greater item in Cybercrime Module 11 on Cyber-Enabled Intellectual Property Crime.
Computer‐related acts causing personal impairment
According to the 2013 UNODC Draft Cybercrime Report, "computer-related acts causing personal damage" include "the use of a computer system to harass, bully, threaten, stalk or to cause fright or intimidation of an individual" (17). Examples of these types of cybercrimes are cyberstalking, cyberharassment, and cyberbullying. These cybercrimes are not included in multilateral and regional cybercrime treaties (eastward.g., the Cybercrime Convention; African Spousal relationship Convention on Cyber Security and Personal Information Protection; and Arab Convention on Combating Information technology Offences).
Cyberstalking, cyberharassment, and cyberbullying take been used interchangeably. Some countries refer to any act that involves the child in either a victim or offender status as cyberbullying (e.m., Commonwealth of australia and New Zealand), while states within the United states use the term cyberbullying to refer to acts perpetrated by and against children. Some countries practise not use the term cyberbullying, but instead employ the term cyberharassment or cyberstalking, or different terms such as cybermobbing (in Austria and Germany) to depict cyberbullying (European Parliament, Citizens' Rights and Ramble Affairs, 2016, 24-25), while others do not use any of these terms. With regards to the latter, Jamaica, for example, prohibits "malicious and/or offensive communications" nether Commodity 9(1) of the Cybercrime Deed of 2015, which criminalizes the use of "(a)…a estimator to send to another person whatever information (whether in the class of a message or otherwise) that is obscene, constitutes a threat, or is menacing in nature; and (b) intends to cause, or is reckless as to whether the sending of the data causes, annoyance, inconvenience, distress, or anxiety, to that person or any other person."
Did you lot know?
In 2017, Latoya Nugent, a human rights activist, was charged with and arrested for violating Department 9 of Jamaica'due south Cybercrimes Deed of 2015, for posting the names of perpetrators of sexual violence on social media. The charges against her were afterward withdrawn. This section of the law, which proscribes online malicious communications, has been criticized for unjustifiably restricting freedom of expression (Barclay, 2017). A similarly worded section of a law in Kenya (Section 29 of the Kenya Information and Communication Human action) was repealed because it was viewed by a national court as unconstitutional due to its vague and imprecise language and its lack of clarity on the types of expression (or voice communication) that would be considered illegal under the Human activity ( Geoffrey Andare 5 Attorney General & ii others, 2016).
Desire to learn more than?
Read Cybercrime Module 3 on Legal Frameworks and Human Rights for a discussion on the relationship between cybercrime laws and human rights.
While in that location are no universally accepted definitions of these types of cybercrime, the following definitions that comprehend essential elements of these cybercrimes are used in this Module and in other Modules of the E4J University Module Series on Cybercrime (Maras, 2016):
- Cyberstalking. The employ of data and communication engineering science (ICT) to commit a series of acts over a period of time designed to harass, badger, attack, threaten, frighten, and/or verbally abuse an private (or individuals).
- Cyberharassment. The utilize of ICT to intentionally humiliate, annoy, attack, threaten, alert, offend and/or verbally abuse an individual (or individuals).
- Cyberbullying. The apply of ICT by children to annoy, humiliate, insult, offend, harass, alarm, stalk, abuse or otherwise assault some other kid or other children.
What differentiates these cybercrimes is the historic period of the perpetrators (i.e., only children engage in and are victims of cyberbullying), and intensity and prevalence of the cybercrime (cyberstalking involves a series of incidents over time, whereas cyberharassment can involve ane or more than incidents). These cybercrimes and their differences are explored in further detail in Cybercrime Module 12 on Interpersonal Cybercrime.
Solicitation or "grooming" of children
Information and communications technologies take been used to facilitate child grooming. Child grooming is the process of fostering rapport and trust through the evolution of an emotional relationship with the victim (Maras, 2016, p. 244). Co-ordinate to Whittle at al. (2013), "grooming varies considerably in style, duration and intensity; ofttimes reflecting the offender's personality and behavior" (63). The offender may dispense the victim using a variety of power and control tactics, including (but not express to): applause, gifts, isolation, intimidation, threats, and/or force (Berlinger and Conte, 1990; O'Connell, 2003; Mitchell, Finkelhor, and Wolak, 2005; Ospina et al., 2010; Maras, 2016) every bit well equally feigning shared interests, or edifice trust past mimicking a child's apparent sense of isolation. Kid training can occur on social media platforms, over email, in chat rooms, through instant messaging services, and via apps, amidst other areas. A 2017 BBC investigation revealed that the Periscope app, which enables live broadcasting anywhere in the world, was being used by predators to groom children. The predators who contacted the children who were broadcasting live fabricated sexualized comments about the children and some even requested children to remove their clothes (BBC, 2017).
 Side by side: Content-related offences
Side by side: Content-related offences
 Back to top
Back to top
Source: https://www.unodc.org/e4j/zh/cybercrime/module-2/key-issues/computer-related-offences.html
0 Response to "Funny Videos of Ceos Misusing Money"
Post a Comment